On 19th July 2024 a software update distributed by CrowdStrike resulted in boot-failure on a huge number of business Windows-running machines worldwide. Recovery took many days in many cases.
The risk of major disruption from security software is underestimated because it's not generally understood that it needs to be given privileged access and so can easily be as disruptive as malware.
CrowdStrike ex-employees: ‘Quality control was not part of our process’ [1]
Use of software such as the above is unnecessary on our machines and ones that we supply, because their native security capabilities are exceptionally effective. In fact many third-party 'security' products for Linux require its awe-inspiring SELinux functionality to be disabled.
"Just because the tiger hasn't bitten you doesn't mean it won't. And when it does it'll hurt."
On conventional business IT systems, by the time you detect signs of a breach it's almost certainly too late to prevent major operational flow disruption and big costs.
Maintaining business OpFlow is what really matters. If only because the cost of disruption prevention is far less than the cost of recovery.
Do facts and reality matter to you? If so, then read on ...
A US IT security company has found that only around 10% of business IT breaches get publicly reported, so the risk is much greater than generally assumed and the safety margins much smaller. It's also still the case that "one wrong click and you're gone".
So there's an urgent need to identify and eliminate the IT safety gaps.
But what incentives to eliminate the gaps do those who sell you 'security' subscriptions have?
Here's some expert opinions. Relevant facts since that 2021 podcast include that Microsoft's annual income from its 'security' subscriptions is now more than USD 20 billion, and many organisations have been highly critical of them, including the US government and others [1] [2].
Ignoring the copious evidence of security problems greatly helps attackers.
Fortunately, and especially for enlightened businesses, we've come up with a highly effective data-flow-maintaining scheme to enable you to stop throwing away money on disruptions.
Your IT support can gradually increase the resilience of your existing IT system, whilst maintaining or increasing productivity. Implement steps yourself or for some enlist the assistance of us or appropriate others.
The full scheme involves using VMs (Virtual Machines), the DF (Desktop Fallback) scheme, the MDFS (Malware Defeating File Sharer), and a range of techniques and recommendations. A powerful aspect of it is that you're in control. You decide how much benefit gets provided.
A fundamental factor is getting security mechanism SELinux:Enforcing widely used because it defeats unknown threats. Don't fear the unknown, because you're already using Linux variants in a range of devices. Our scheme is based on Enterprise variants of it, which for a long time have also been used on a huge number of servers.
Do you want your business to remain operational in spite of malware outbreaks or security software faults?
Do you want the competitive advantage of publicising that you've moved to an exceptional IT scheme that protects both productivity and data?
If so, please get an overview of what's involved from what follows, and then make a start by telling us which parts of the scheme you need our services for, and the types (workstation or server) and numbers of computers involved.
DF is about also having available Alternative Desktop computers that can handle your business data, and which are naturally immune to Windows malware. Meaning that when such malware invades or faulty 'security' software arrives, your business can remain operational regardless. Details here.
Version 1.2 website shown. Currently at v2.1 - More options and dark theme.
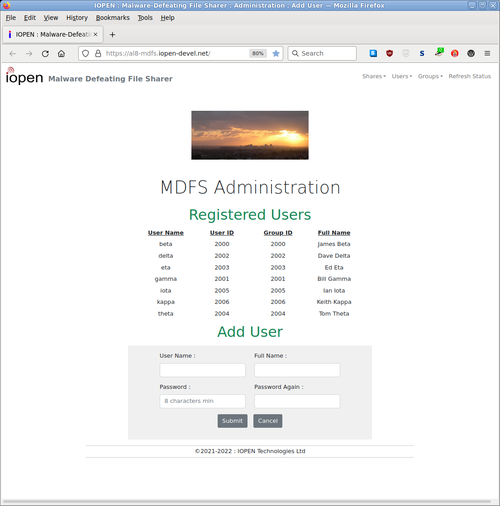
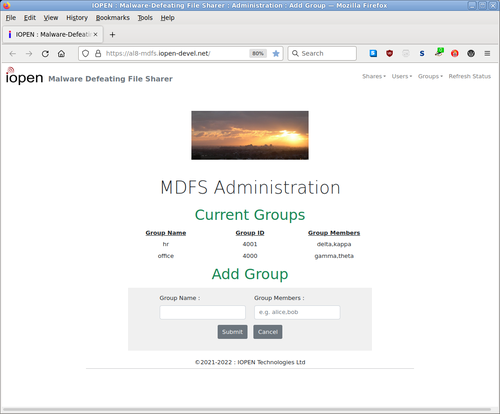
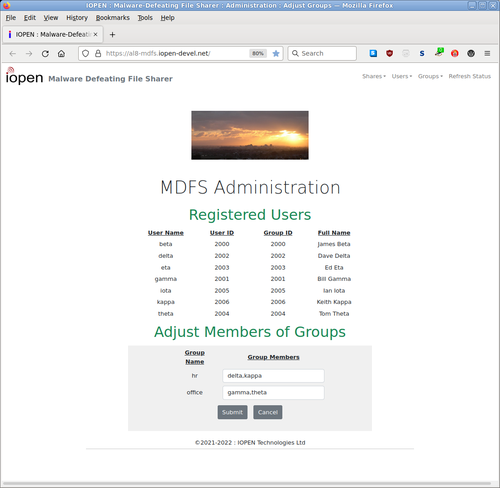
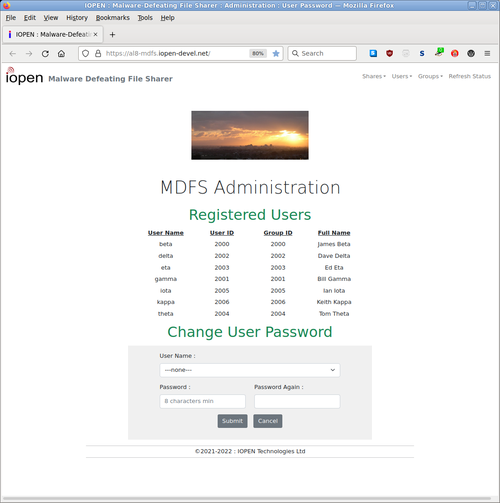
MDFS is compatible with MS-Windows sharing, but is itself naturally immune to Windows malware, and it doesn't need or use third-party 'security' software.
- Gives you competitive advantage via enabling you to publicise your exceptional commitment to protecting data and productivity.
- Complements Desktop Fallback by remaining operational and able to provide Alternative Desktops with operational data.
- Being much more effective than insurance.
- Being safer, and more reliable and economical than using 'The Cloud'.
- Having unlimited users and not having Client Access Licences.
- Providing simple administration of users and shares using a web browser.
- Having long-term viability via being based on mainstream technology.
- See also our Client Experience and Graduated Benefits documents.
- Actually, there is no 'Cloud'. There's just computers owned and controlled by others. [ 1, 2 ]
- Being an MS-Windows compatible File Sharer that is naturally immune to Windows malware because it doesn't use Windows itself.
- Complements Desktop Fallback by remaining operational and able to provide Alternative Desktops with operational data.
- Not needing or using third-party 'security' software, or so-called 'AI'.
- Having its own robustness greatly enhanced by the very powerful SELinux security mechanism which, amongst its many capabilities, can defeat unknown exploits.
- Having support provided by a pool of trustworthy experts from at least 4 compatible IT businesses, via a dedicated remote support channel (VPN) that uses quadruply-secured (4FA) access.
- Providing secure backup via a dedicated channel (VPN) : Overview and Options.
- Having automated monitoring, reporting, and alerting.
- Being provided as a Virtual Machine that runs an Enterprise Linux.
- Having straightforward Windows Domain integration, where needed. But we recommend avoiding doing so if at all possible so that MDFS remains fully usable when your Domain Controllers get taken down.
- All local DHCP and DNS servers should be run by non-Windows machines, for the same reason as not joining a domain.
- Remote support is required to be done from non-Windows machines.
- See also our Graduated Benefits and MDFS Structure documents.
- Improve resilience further by having Warm Spare VMs.
In the generating of any critical system, correctness, completeness, and consistency are vital.
So we've put a lot of effort into developing and verifying software that automates the generating of customised VMs for clients. Based on a small plain-text specification file for each VM. MDFS is just one of the function-types of VM that the software can generate. Another is a VoIP PBX.
It can also generate customised non-VM items such as the Hypervisor and the .iso file for doing remote installs.
The system-generating software is run on dedicated isolated VMs. Customisations include generating unique passwords and security keys for each client VM.
We can provide a free MDFS Test Drive for potential business clients. English-speaking ones initially.
Each Test Drive starts with a fresh MDFS VM running on our server. You'll need to install a Wireguard VPN client on your workstation and configure it to connect to the VM. We provide configuration details.
To make efficient use of resources we respond to what we consider to be credible requests from businesses. So if a Test Drive interests your business please make a request containing some details of your IT situation.
Implementing our full solution will save some adoptees millions of dollars, and in some cases save the business itself. Because copious evidence [ 1, 2, 3, 4 ] supports the assertion that for business users of MS-Windows the question is when, not if, a major malware-related operational disruption will occur.
You're sceptical that MDFS (in particular) can do what nobody else seems able to do reliably.
Well, MDFS is non-Windows so we don't have to contend with the 'Windows high background-noise level'. Giving us an excellent Signal-to-Noise Ratio (SNR) when looking for signs of workstation malware 'playing with' the shared files.
Its own robustness is greatly enhanced both by being naturally immune to Windows malware and by using SELinux in Enforcing mode. Note that MS-Windows still doesn't have any mechanism that's even close to SELinux's capabilities.
Background information and FAQs are here.
Terms and Conditions are here.
To avoid giving potential attackers more clues here, you'll need to request further details.
©2021-2025 : IOPEN Technologies Ltd - NZ